

Master Password is an "unconventional" way of managing passwords. If you've got questions and need answers, read on. For a full overview of the security features in this app, see the Security page. For the technical details on how Master Password works, see the Algorithm page.
There are ways around everything, including Master Password's algorithm. A hacker could install a program on your computer that watches as you send your password to the website. At this point, however, no amount of password management will help you, if this is your worry, you need to use two-factor authentication methods which most sites don't support.
A hacker could also attempt to derive your master password from a password stolen from a site. Master Password has been designed specifically to thwart any attempts to break its security model. For more information, read "Why Is Master Password Strong?".
Master Password has been engineered not to store any secrets on your phone. The secret is your master password and it is only in your head. You enter it when opening the app at which point Master Password remembers it only as long as you leave the app open. Once you ask the app for a site's password, your master password is used to calculate the site's password.
To answer the question directly: not unless the app is showing at the time he steals your phone, or you configured it to save the master password and used a weak PIN on your phone.
There is an exception: Master Password allows you to save "custom" or "personal" passwords in the app. These passwords don't use Master Password's special algorithm and are merely encrypted using the strong master key derived from your master password. These types of passwords behave more like conventional vault-based passwords do. They are however very well protected and an attacker would still need to find a way to crack your master password (which is extremely difficult, see below) before being able to decode the passwords in its vault.
Cryptography only provides technical security. It does not protect you from situations where you are legally required or forced by peers to surrender your key.
In fact, many countries provide their officers with a legal grounds for forcing you to divulge your encryption keys to any encrypted information they've recovered during a warranted search.
Again, unlike ordinary password managers, Master Password might have an edge here. If you make no use of stored passwords, Master Password doesn't actually encrypt anything with your master password. That means, when your devices are seized, these legal grounds may no longer apply. Note however that this does not constitute legal advice and that this theory has never been tested in practice.
For your safety, we recommend that in preparation of travelling, you change the master password for your user on the device. That way, if your device is seized by a foreign entity and they force you to divulge your master password, you'll likely be fully compliant by simply giving up the new master password even though it will cause the app to generate invalid passwords for all your sites. Later, you can always change the master password back to the real one.
The simple answer to that question is: First and foremost, memorable and unrelated to you. What that means is that the most important thing about your master password is that you need to be able to recall it any time and yet it should not be derived from anything personal.
That advice usually doesn't help very much with actually picking a good master password. The goal of a good password is that it'll take an attacker a lot of guesses before he'll find it. That is the core idea behind good passwords.
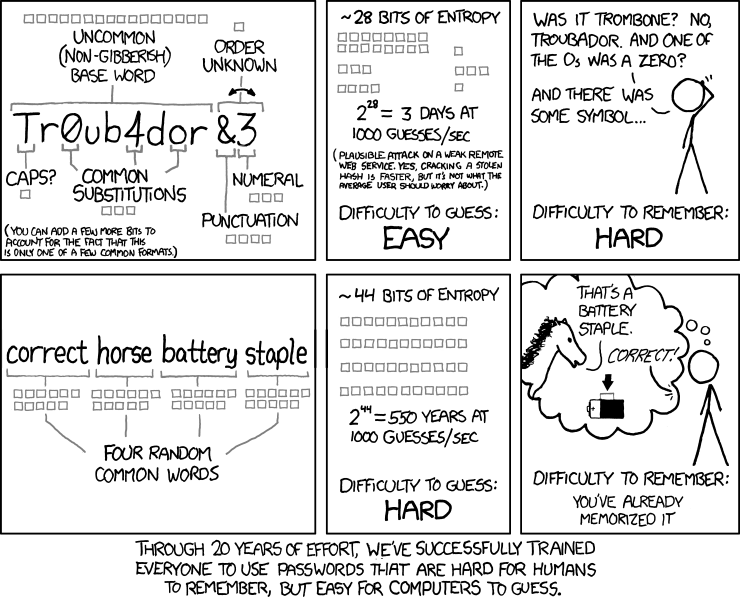
There are a few strategies of getting good passwords. The speed with which an attacker can guess your password depends a lot on whether he knows what kind of password you're using or not. So we'll compare a few password strategies, their strength and how memorable they are.
The simplest strategy for picking good passwords is by just picking a bunch of random letters, digits and symbols and mixing them up. This is a great strategy for strong passwords but those passwords are usually not very memorable.
Another strategy is by "encoding" something you already know. This can seem like a good way to make memorable passwords, but recalling the "encoding" you used two years later can be tricky. This also makes it much easier for attackers that know you to find your password.
Master Password itself generates very random passwords that look semi-legible, for instance Togu3]ToxiBuzb. Such passwords have been found to be very memorable while also being very high in entropy (hard to guess).
A strategy that's gaining traction lately is that of combining words into a sentence. Some claim it's best for the sentence to make no grammatical sense, others dispute these claims. It's a fact, though, that if your attacker doesn't expect such a password, they're nearly impossible to defeat.
Let's sum these strategies up in a table, note that this type of comparison is very subjective.
| Strategy | |||
|---|---|---|---|
| Example | Time to crack (bulk/ignorant attack) |
Time to crack (attacker knows strategy) |
Memorability |
| Random password, 4 number PIN | |||
9174 |
50 minutes | 50 minutes | Moderate |
| Random password, 4 alphanumeric characters | |||
a1qd |
1.7 months | 1.7 months | Difficult |
| Random password, 6 alphanumeric characters | |||
v9ea30 |
560 years | 560 years | Difficult |
| Encoding a word, Tr0ub4dor style | |||
Tr0ub4dor |
2.6 years | 2.6 years | Moderate |
| Master Password style | |||
Togu3]ToxiBuzb |
> age of the universe | 632 million years | Moderate |
| Nonsense sentence, correct horse style | |||
correct horse battery staple |
> age of the universe | 173 thousand years | Moderate |
| Real sentence, 4 words (1 verb, 1 noun) | |||
I have a dream |
> age of the universe | 8.7 months | Easy |
| Real sentence, 4 words (1 adjective, 2 nouns) | |||
My red beach ball |
> age of the universe | 551 years | Easy |
| Real sentence, 6 words (1 adverb, 1 verb, 1 adjective, 1 nouns) | |||
I once had a red ball |
> age of the universe | 27 thousand years | Easy |
The numbers on sentences assume the attacker thinks you know no more than 500 adjectives, 2000 nouns, 333 verbs and 300 adverbs. These calculations are very subjective, since language is such a complex thing to write a password cracker for. Never mind adding in punctuation, names or using other languages.
Pick a strategy that works best for you, but remember that far more important than maximizing the "time to crack" is making your master password memorable and impersonal.
The time-to-crack numbers throughout this website are based on the following assumptions:
1 479 million SHA-256 hashes per second (hashcat on AMD HD 6990)3.3 Master Password passwords per second (2GHz MacBook Pro, scrypt N=32768, r=8, p=2, dkLen=64).Don't hesitate to send us a message at masterpassword@lyndir.com. I'll get right on your case. Try to include any details you can. Good or common questions will have their answers added to this page.